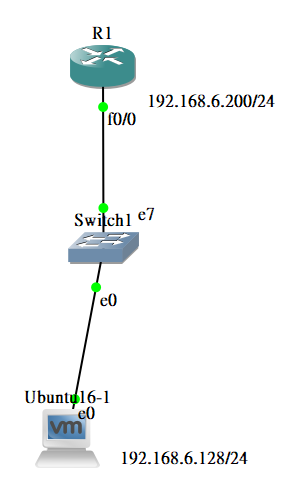
拓樸
官網說明,啟用 SSH 需要四個步驟:
- 配置
hostname - 配置
DNS domain - 產生要使用的
SSH key vty啟用SSH transport表明支援
SSH 與 telnet 比較之下,重點在於 SSH 有加密的機制,因此在傳遞資訊方面較為安全。
R1 設定
介面卡設定
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface fastEthernet 0/0
R1(config-if)#ip address 192.168.6.200 255.255.255.0
R1(config-if)#no shutdown
*Mar 1 00:03:03.563: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:03:04.563: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
SSH 設定
R1(config)#ip domain-name itachi.com # 定義域名
R1(config)#crypto key generate rsa general-keys modulus 1024 # 產生 RSA key
The name for the keys will be: R1.itachi.com
% The key modulus size is 1024 bits
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
R1(config)#
*Mar 1 00:05:13.471: %SSH-5-ENABLED: SSH 1.99 has been enabled
R1(config)#ip ssh time-out 15 # 登入此設備時,15 秒內無動作則在輸入一次
R1(config)#ip ssh authentication-retries ?
<0-5> Number of authentication retries
R1(config)#ip ssh authentication-retries 2 # 驗證失敗次數
R1(config)#ip ssh maxstartups 3 # 限制能夠連線到此設備數量
R1(config)#ip ssh port 2222 rotary 1 # 更換 port 號,rotary 1 對應的 port 號為 2222
R1(config)#ip ssh version ?
<1-2> Protocol version
R1(config)#ip ssh version 2 # SSH Version
遠端介面設定
R1(config)#username itachi privilege 15 password 123456
R1(config)#line vty 0 4
R1(config-line)#rotary 1 # 0 - 4 介面都藉由 2222 port 登入
R1(config-line)#login
R1(config-line)#login local # local 下資料庫驗證
R1(config-line)#privilege ?
level Assign default privilege level for line
R1(config-line)#privilege level ?
<0-15> Default privilege level for line
R1(config-line)#privilege level 15
R1(config-line)#transport input ssh # 預設 vtys 的傳輸是 Telnet,限制只有 SSH 能夠連線 0 到 4
R1#wr
Building configuration...
[OK]
驗證 SSH
1#show ip ssh
SSH Enabled - version 2.0
Authentication timeout: 15 secs; Authentication retries: 2
ubuntu ssh 遠端 R1
因為 cisco 的加密方式有點不安全,在 ubuntu SSH 配置上預設無該演算法,因此必須加 -oKexAlgorithms=+diffie-hellman-group1-sha1 參數。
cch@ubuntu:~$ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -l itachi -p 2222 192.168.6.200
The authenticity of host '192.168.6.200 (192.168.6.200)' can't be established.
RSA key fingerprint is SHA256:MrBhp+LzbnJyQoTFU1LURcpwLaN1aZxha0+YykOPf3k.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.6.200' (RSA) to the list of known hosts.
Password:
R1#sh
R1#show ip int
R1#show ip interface br
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 192.168.6.200 YES manual up up
Serial0/0 unassigned YES unset administratively down down
FastEthernet0/1 unassigned YES unset administratively down down
Serial0/1 unassigned YES unset administratively down down
Serial0/2 unassigned YES unset administratively down down
FastEthernet1/0 unassigned YES unset administratively down down
Serial2/0 unassigned YES unset administratively down down
Serial2/1 unassigned YES unset administratively down down
Serial2/2 unassigned YES unset administratively down down
Serial2/3 unassigned YES unset administratively down down
R1#
R1 查看介面狀況
查看 SSH session
R1#show ssh
Connection Version Mode Encryption Hmac State Username
0 2.0 IN aes128-cbc hmac-sha1 Session started itachi
0 2.0 OUT aes128-cbc hmac-sha1 Session started itachi
%No SSHv1 server connections running.
顯示當前 session
R1#show line vty 0 4
Tty Typ Tx/Rx A Modem Roty AccO AccI Uses Noise Overruns Int
* 162 VTY - - 1 - - 6 0 0/0 -
163 VTY - - 1 - - 0 0 0/0 -
164 VTY - - 1 - - 0 0 0/0 -
165 VTY - - 1 - - 0 0 0/0 -
166 VTY - - 1 - - 0 0 0/0 -
show users 顯示登入該設備的使用者
R1#show users
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
162 vty 0 itachi idle 00:03:00 192.168.6.129
Interface User Mode Idle Peer Address
Wireshark

上面圖片有過濾。在相互使用 SSH 通訊前通常 SSH 使用 TCP 作為傳輸協定。
165 和 166 個封包為 SSH 版本交換
165 至 178 個封包,首先先發出 Key Exchange Init,相互告訴對方自己的加密演算法、MAC 演算法等等